Over 95% of data breaches are avoidable.
Interviews with individuals that conduct cyber-attacks for a living stated that their preferred targets are the easiest.
The company that leaves their doors and windows open are more likely to be exploited. uRISQ's Threat Scanning performs a recurring vulnerability scan on your website and firewall, making you aware of your open doors and windows.

Threat Scanning
Vulnerability scanning is an important part of any security and privacy program.
uRISQ Threat Scanning automates the scanning for you.
HOW TO VIDEOS
Threat Scanning
Perform vulnerability scans on your website and firewall. Close the access points nefarious actors are looking for. Set up in less than 1 minute and start locking those virtual doors.
- Register on uRISQ
- Enter in website and firewall IP address
- Wait for scan result email
- Document compliance activities
Registration
Threat Scanning
Policy Center
We want to hear from you to make uRISQ the best solution for small to medium-sized businesses. Our customer support philosophy is based on listening to our customers and providing them with the answers and easy solutions to use. If you have a question and do not find the answer, send us a note using the form below.

-
Why do I need website and firewall scanning?
You choose to lock the doors and windows to your house to deter someone from coming and stealing from you. uRISQ's Threat Scanning module is your automatic check to ensure those virtual front doors and windows are closed. 95% of all data breaches are avoidable, and the easiest targets are those that don't have their doors locked.
-
After setup do I have to do anything to get my scan?
After setting up your Threat Scanning settings, your scan request will automatically go into our scanning queue. You will receive an email when each of your scans is complete. After your first scan, your website and firewall will automatically be scanned every month. You will receive an email after completion, identifying if there are any changes.
-
What are the notes for?
uRISQ is designed to be a central area for your organization to document your compliance activities. Once set up, uRISQ's Threat Scanning automatically performs a vulnerability scan, doing most of the work. The notes are for you or your IT Professional to document the resolution of vulnerabilities, reasons for the finding, and acceptance of risk. This is important to show proof of a program in place when legal inquiries occur.
-
What do I do if the scan comes back with changes?
Changes do not necessarily mean something is wrong. However, it does mean something needs to be reviewed, and a note needs to be added. A change could be an implemented fix, but it can also mean that a new vulnerability was found. We recommend that you click on the link in the email and log into uRISQ to view the report details. Contact your IT Professional or your Web Developer to address and understand the vulnerabilities found.
-
Can I send the report to my developer or my IT resource?
You can easily add a new user associated with your account and assign them as a Threat Scanning user. This will ensure they get the scan reports so they can address the issues promptly. Go to the Help Center to get steps on how to add a new user to your account.
-
Will the scans hurt my website or firewall?
Our scans are designed to find vulnerabilities without being intrusive. Threat Scanning should not bring down your website or firewall. You may have to allow access depending on the level of intrusion detection you may have in place.
-
Can I stop a scan once I add it into my settings?
You can easily remove the website or IP address in your settings to stop a scan. If the scan has not started, it will be removed from our scan queue, and no scan will be performed.
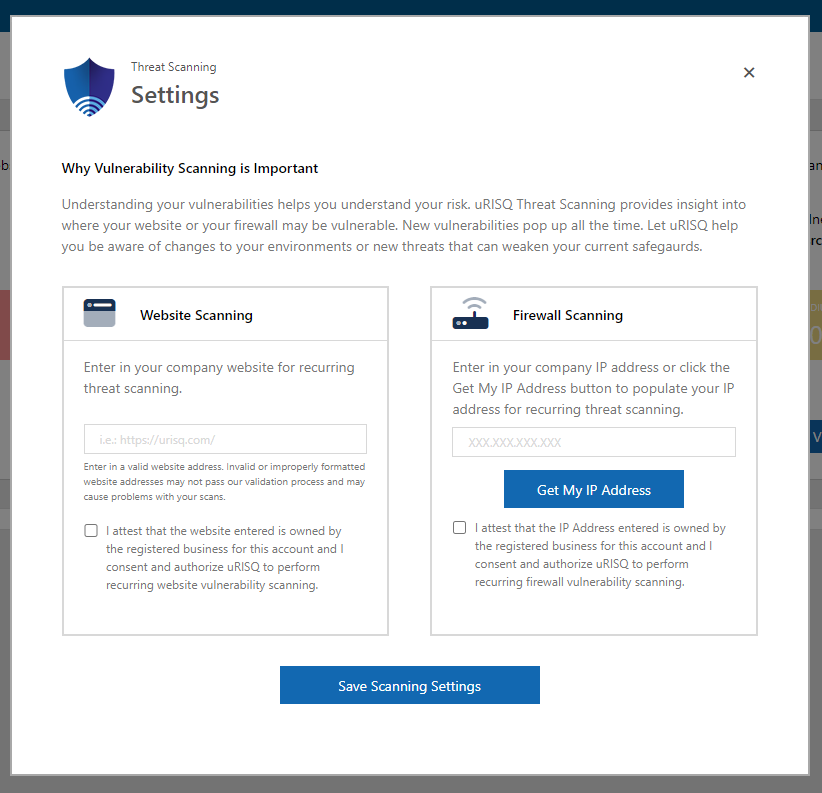
We believe that setting up Threat Scanning is the quickest way to see where you may have vulnerabilities and risks, so we have made it easy. When you log in, if you have not configured your Threat Scanning module, uRISQ will open up the Threat Scanning setting window automatically. You can also access it by going to the Threat Scanning section and clicking on Settings.
You can enter your website or web application address you wish to scan. Firewall scanning is even easier. If you are at the office, click the “Get My IP Address” button. It will populate the IP address you are currently at. To save your settings, you must attest that you own and are authorized to set up these scans and then click the “Save Scanning Settings” button.
Congratulations, you have just started your first vulnerability scan. Your scans are in our queue and will be processed in the order scans were submitted. You will receive an email as soon as your scans are complete.
Website Scanning
Scanning for vulnerabilities within your website and firewall is important. However, technology is evolving not as quickly as nefarious actors are hitting your business. Data is the preferred currency of these actors, and it is your responsibility to protect the data you collect for your customers and employees.
uRISQ’s Website Scanner will scan for all known vulnerabilities, focusing on security and impact. uRISQ provides scan results in an easy-to-read report that easily identifies vulnerabilities and categorizes them into high, medium, low, and informational. In addition, our scan will assess your site against the OWASP Top 10, which focuses on the top 10 web application security standards.

Firewall Scanning
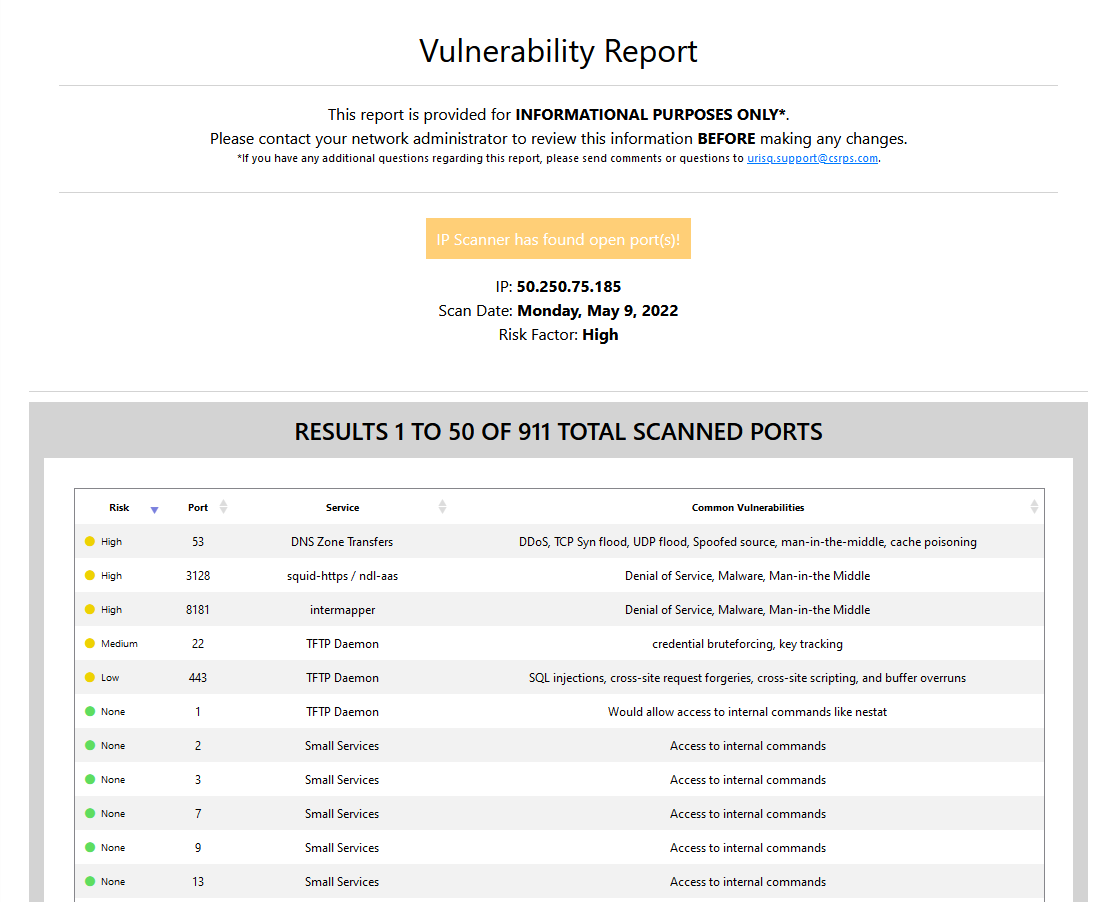
uRISQ’s Firewall Scanning scans 911 ports on your public firewall. A noninvasive scan will check which ports are vulnerable to cyber-attack. After every scan, you will receive an email identifying changes to your firewall, so you only focus on needed remediation, saving you precious time.
Your firewall report will highlight the vulnerable ports and identify the common vulnerabilities for each port. Knowing what you have open and taking action to close those openings if they are not necessary is a giant step forward to avoiding a data breach.
Compliance Log
Along with every scan, you have the ability to document your compliance activities. uRISQ automatically scans your website and firewall once set up, which is an automatic compliance activity. You simply review changes found to document your remediation actions or acceptance of risk.
Questions about uRISQ? We want to hear from you.


